All Projects
A collection of my work and research
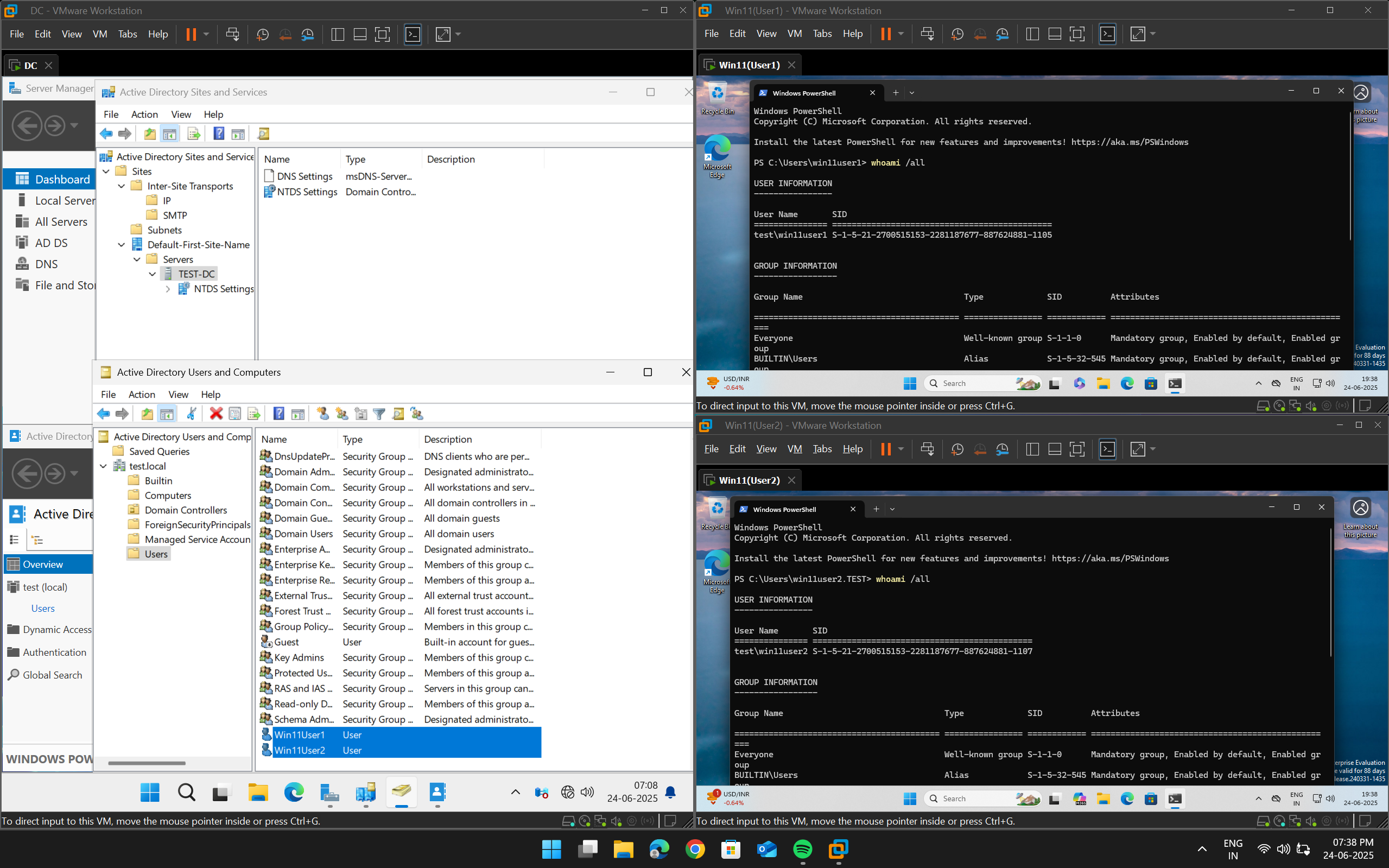
AD Lab Attack Simulation
Designed a lab to simulate AD attacks like Kerberoasting and Pass-the-Hash.
View Project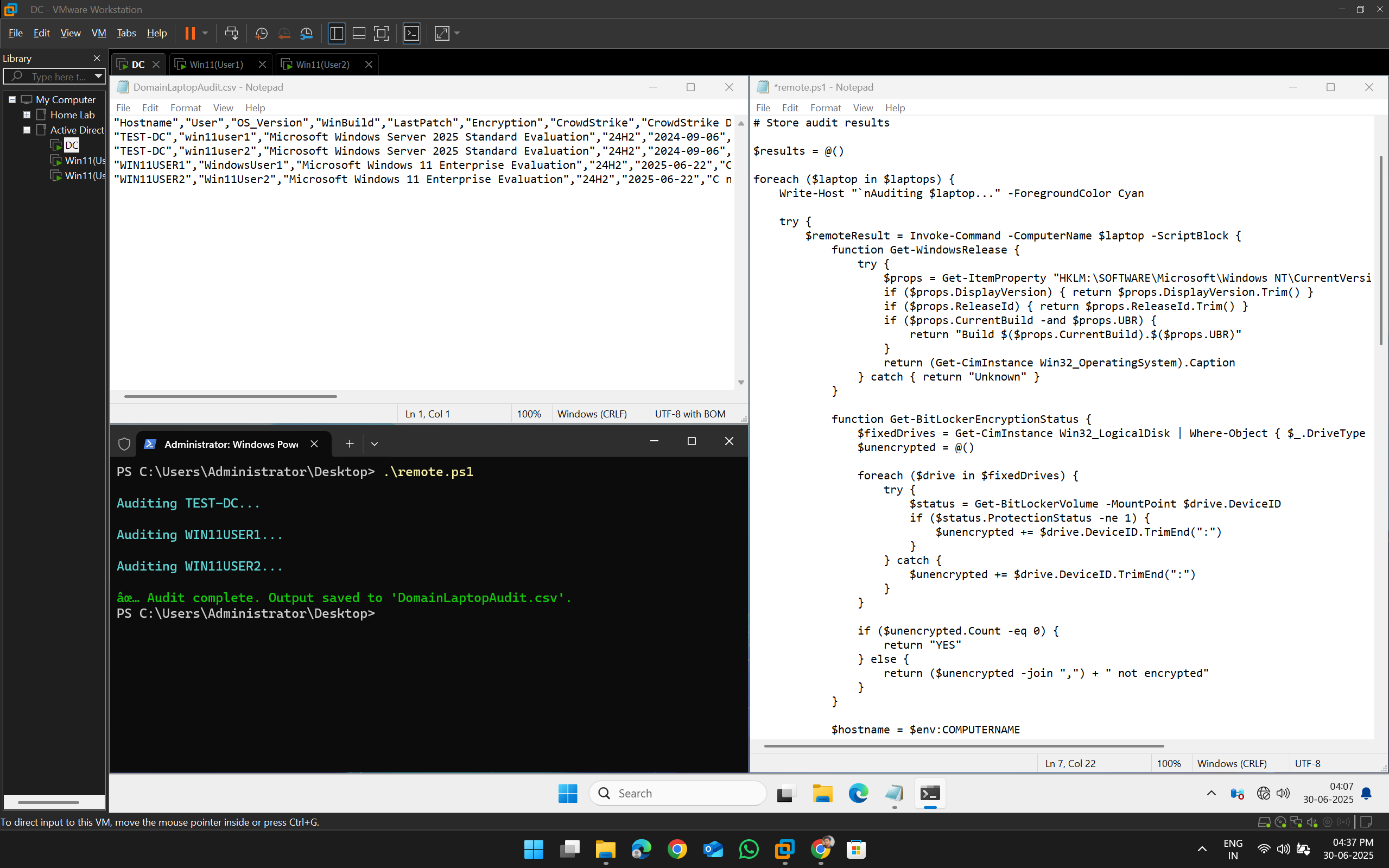
Automated Security Auditing
A system to automate security audits for OT and IT environments.
View Project
Hack Windows with Discord
exploit Discord as a Command-and-Control (C2) channel to remotely control compromised Windows systems
View Project
Dynamic Malware Sandbox
A custom sandbox for analyzing malware behavior and network traffic.
View Project
AWS Security Auditor
A script to audit AWS for common security misconfigurations.
View ProjectMemory Forensics Toolkit
Scripts to automate memory dump analysis using Volatility.
View ProjectSecurity Log Analyzer
A Python tool to parse and analyze logs for suspicious activities.
View ProjectVulnerable Web App
A deliberately vulnerable web app to practice exploiting common flaws.
View ProjectIDS/IPS Implementation
Deployed and configured Suricata for network intrusion detection and prevention.
View ProjectCustom Encryption Algorithm
Developed a simple symmetric encryption algorithm in Python for educational purposes.
View ProjectSocial Media Footprinting Tool
A tool to gather publicly available information from various social media platforms.
View ProjectCrackMe Challenge Write-up
Detailed analysis and solution for a reverse engineering challenge using Ghidra.
View ProjectPhishing Campaign Simulator
Created a controlled phishing campaign to test and improve security awareness.
View ProjectSmart Device Vulnerability Scan
Performed a security assessment of a popular IoT device, identifying several vulnerabilities.
View ProjectAutomated Reconnaissance Script
A Bash script to automate initial reconnaissance steps for bug bounty hunting.
View ProjectIoC Feed Aggregator
A tool to aggregate and de-duplicate Indicators of Compromise from multiple public feeds.
View Project